How It Works - Countermark
Why Countermark
QR code versus Countermark
QR codes were developed in 1992; they contain the entire text to be used, for example a website URL. A summary below gives the key differences between Countermark and QR codes.
Countermark codes are controlled by us, and have strong inbuilt anti-spoofing technology. QR codes are detected and read automatically by contemporary phones. This means counterfeiters can use their own QR codes on fake products and take your customers to fake websites to request their usernames and passwords.
Countermark codes have in-built GDPR compliant processing and, subject to permissions, can identify the person reading the code, their location, their phone model and the product they are checking. QR codes have no GDPR protection, meaning codes that link back to your website have little in the way of customer data.
Countermark codes are inherently human and machine-readable, so, in environments where the code can be scuffed or damaged, the user can enter strings of digits from the top row to recover from a no-read situation. A damaged QR code cannot be recovered in this way.
Countermark codes were designed to be printed with Continuous Ink Jet Printers, already a mainstay of food and industrial production. Countermarks can be ink-jetted onto metals and plastics. QR codes require a strong black/white contrast, meaning they may need to be printed onto a label. That label then needs to be stuck onto the product, costing much more that direct printing. Using Countermark codes therefore avoids the need to securely source, handle and apply labels.
Countermark codes can be disabled or enabled based on location, age of the code or a change in the marketing message. QR codes don’t have this inherent level of control.
Countermarks codes can also be enabled according to the status of the person reading the code. A field service technician could be given repair data or service history, whereas a customer reading the same Countermark can receive marketing data.
Fast, simple and effective, Countermark is an invaluable tool for checking authenticity and validation.
How are Countermarks created?
Countermarks are created by Countermark servers hosted in the Microsoft Cloud. The Issuer logs on to their account, decides the type and quantity of Countermarks needed and our software does the rest.
Countermarks can be produced in a range of formats depending on how the Countermark is to be printed. Available formats are:
- PNG files for use in Microsoft Office programs
- CSV dot files for laser marking onto plastic and similar materials
- CSV character files for GIS software, used for industrial inkjet printers
- Special files (eg for Lynx Continuous Ink Jet Printers) are also available
Once a Countermark is created, all Countermarks are stored safely on our encrypted servers, hosted on Microsoft Cloud. Security is extremely important to us and you can be confident that all data held is protected and encrypted.
How is data attached to a Countermark?
Interactive panels in the Countermark website allow Issuers working with Microsoft Office programs to attach data to Countermarks, define the style of their Countermarks and produce Countermarks that can be copied and pasted into Office, Adobe Acrobat and similar programs.
Countermarks produced in bulk for industrial use have no attached data. These Countermarks are typically configured when the Countermark is used, for example when a Countermarked Tag is associated with a product, the consignment note or other data can be added to the Countermark as the tag is fixed to the product.
How is a Countermark read?
The free Countermark App, installed on a mobile device with an internet connection, is all that is needed to read the Countermark and check the authenticity of your document or product.
Using the Countermark App, the mobile device scans the Countermark and the App performs a security check to ensure that the user has the authority to read the Countermark. The checks can include confirming:
- the identity of the mobile device user
- the location of the user (using the mobile device location data)
- the age of the Countermark
Following these checks, the user is then given access to specific information, such as confirmation that the Countermark is valid.
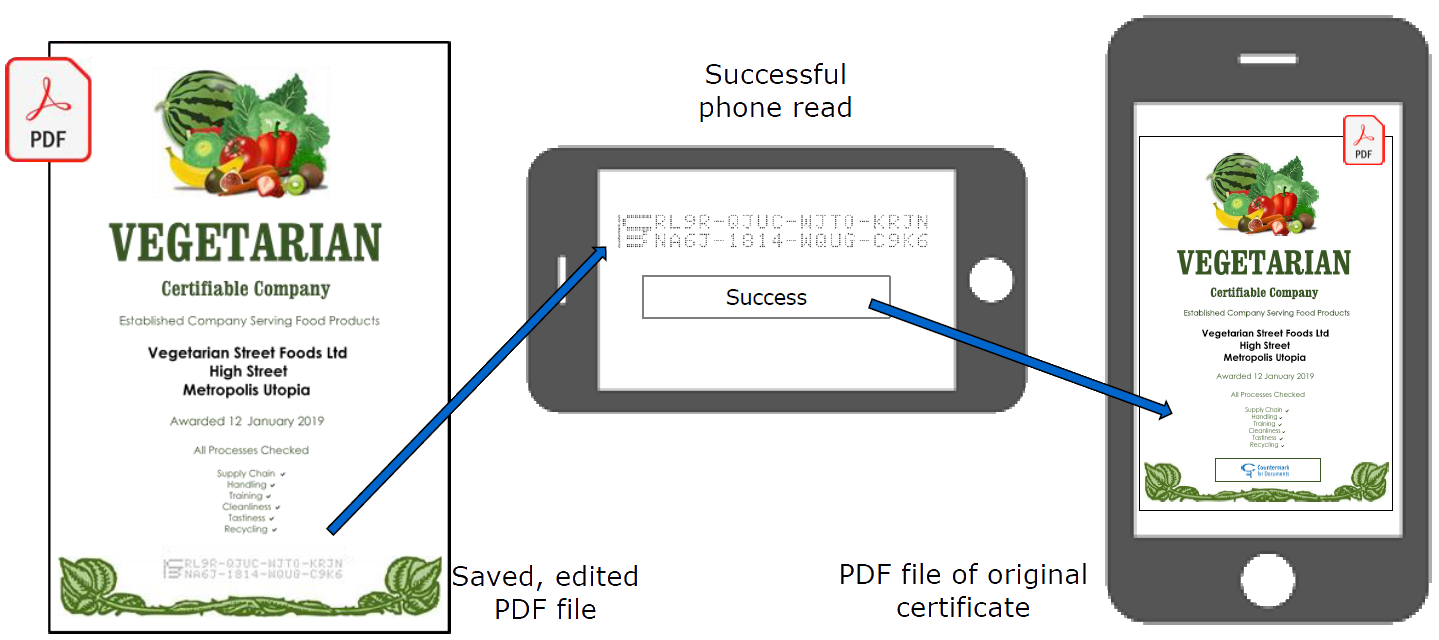
When a certificate containing a Countermark is read by an individual, their phone will receive a copy of the original certificate in PDF format.
What does the Countermark Issuer receive?
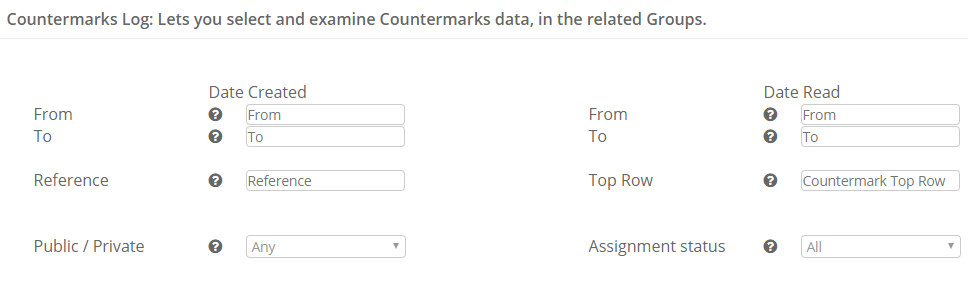
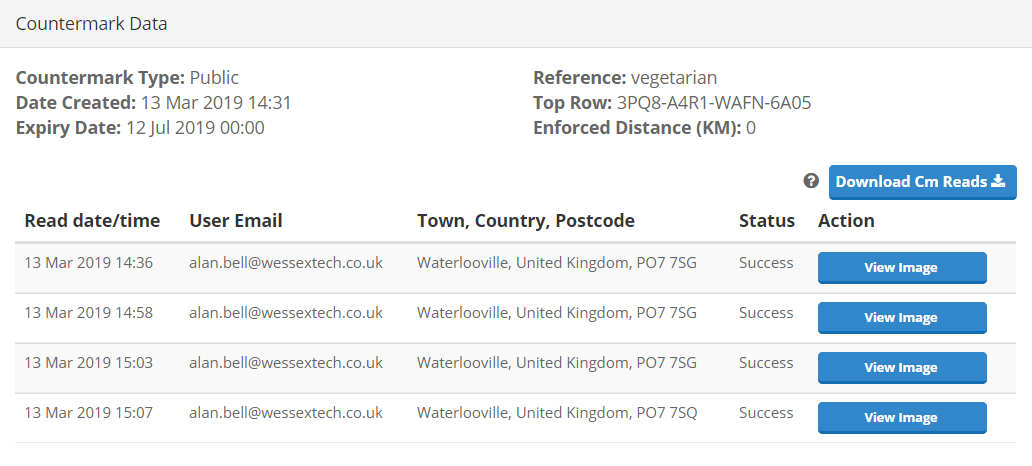
You will have access to a various searchable analytics data which can be used for marketing or market research purposes. For example, you can track where a component has been installed from the end user’s data and this can be used for a targeted sales approach close to replacement time. Similarly, if a document or certificate requires renewal, reminders can be sent.
Ultimately, brand owners can track their products through the supply chain and identify the end users by using Countermark technology. This information allows brands to find new ways to market to product users and can highlight supply chain delays and potential grey market diversion.
Countermark is GDPR-compliant, with the necessary permission requests included for the use of Countermark technology.
What does the Countermark App user receive?

The end user of Countermark receives peace of mind. When a certificate containing a Countermark is read by an individual, their phone will receive a copy of the original certificate in PDF format. Quick and easy to use, Countermark gives rapid confirmation that the genuine product has been supplied - or not!



